Cisco1721とRTX1000でのIPsecができたので1812Jとも接続してみました。
そのまんまでつながるわけなんですが、SVIインターフェースのVLAN1の扱いにちょっと悩んだというか…
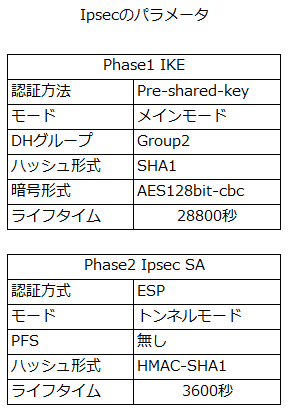
今回の構成図
まえとほぼ同じですね~
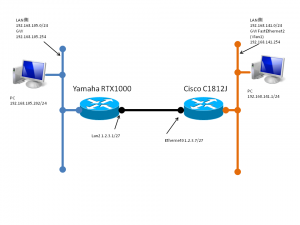
IPsecVPNのパラメータ
これも同じ
以下がCisco1812Jのコンフィグ
version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname C1812J-01 ! boot-start-marker boot-end-marker ! enable password kumakuma ! no aaa new-model ! resource policy ! ! ! ip cef ! ! ! ! ! ! ! ! crypto isakmp policy 1 encr aes authentication pre-share group 2 lifetime 28800 crypto isakmp key password1234 address 1.2.3.1 ! ! crypto ipsec transform-set DEFAULT esp-aes esp-sha-hmac ! crypto map LAB local-address FastEthernet0 crypto map LAB 1 ipsec-isakmp set peer 1.2.3.1 set transform-set DEFAULT match address 100 ! ! ! ! interface FastEthernet0 ip address 1.2.3.7 255.255.255.224 duplex auto speed auto crypto map LAB ! interface FastEthernet1 no ip address shutdown duplex auto speed auto ! interface BRI0 no ip address encapsulation hdlc shutdown ! interface FastEthernet2 ! interface FastEthernet3 ! interface FastEthernet4 ! interface FastEthernet5 ! interface FastEthernet6 ! interface FastEthernet7 ! interface FastEthernet8 ! interface FastEthernet9 ! interface Vlan1 ip address 192.168.141.254 255.255.255.0 ip tcp adjust-mss 1350 ! ip route 0.0.0.0 0.0.0.0 1.2.3.1 ! ! no ip http server no ip http secure-server ! access-list 100 permit ip 192.168.141.0 0.0.0.255 192.168.105.0 0.0.0.255 ! ! ! ! ! ! control-plane ! ! line con 0 line aux 0 line vty 0 4 password alpha0 login ! ! webvpn context Default_context ssl authenticate verify all ! no inservice ! end
1812J側でのIPsecVPN接続確認
まずはshow crypt isakmp saの結果を確認します。
正しい例
1812J#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id slot status 1.2.3.7 1.2.3.1 QM_IDLE 2003 0 ACTIVE 1.2.3.7 1.2.3.1 QM_IDLE 2002 0 ACTIVE 1.2.3.7 1.2.3.1 QM_IDLE 2001 0 ACTIVE
Yamaha RTX100のコンフィグ
ip route 192.168.141.0/24 gateway tunnel 2 ip lan2 address 1.2.3.1/27 tunnel select 2 ipsec tunnel 102 ipsec sa policy 102 2 esp aes-cbc sha-hmac ipsec ike duration isakmp-sa 2 28800 ipsec ike encryption 2 aes-cbc ipsec ike group 2 modp1024 ipsec ike hash 2 sha ipsec ike local address 2 1.2.3.1 ipsec ike local id 2 192.168.105.0/24 ipsec ike pre-shared-key 2 text password1234 ipsec ike remote address 2 1.2.3.7 ipsec ike remote id 2 192.168.141.0/24 ip tunnel tcp mss limit 1350 tunnel enable 2 ipsec auto refresh on
show crypt ipsec saの出力を確認します。
正しい例
1812J#show crypto ipsec sa
interface: FastEthernet0
Crypto map tag: LAB, local addr 1.2.3.7
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.141.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.105.0/255.255.255.0/0/0)
current_peer 1.2.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 109, #pkts encrypt: 109, #pkts digest: 109
#pkts decaps: 2353, #pkts decrypt: 2353, #pkts verify: 2353
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.2.3.7, remote crypto endpt.: 1.2.3.1
path mtu 1500, ip mtu 1500
current outbound spi: 0xC43838B1(3292018865)
inbound esp sas:
spi: 0xF96E0BEC(4184738796)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: Motorola SEC 2.0:1, crypto map: LAB
sa timing: remaining key lifetime (k/sec): (4483123/2577)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC43838B1(3292018865)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: Motorola SEC 2.0:2, crypto map: LAB
sa timing: remaining key lifetime (k/sec): (4483386/2575)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
双方のクライアントマシンでpingを打ち続けるとカウントが増えていきます。Yamaha側の確認
正しい例
RTX1000# show ipsec sa sa sgw connection dir life[s] remote-id -------------------------------------------------------------------------- 1 2 isakmp - 28295 1.2.3.7 3 2 tun[002]esp send 28297 1.2.3.7 4 2 tun[002]esp recv 28297 1.2.3.7 5 2 isakmp - 28298 1.2.3.7 6 2 isakmp - 28299 1.2.3.7
